
Rencons Construction & Heavy Industry: Tracking Real-Time Developments on Construction Sites with Drone Imagery
The construction industry is in the midst of a digital transformation, with emerging technologies redefining traditional methods and processes. One...

DeepFake ile Canlı Görüşmeleri Hackleme: Eğlence mi, Yoksa Tehlike mi?
Son zamanlarda finansal kayıplara neden olan ve kurum güvenliğini tehlikeye atan yeni bir tehdit türüyle karşı karşıyayız: Deepfake. Deepfake, yapay...
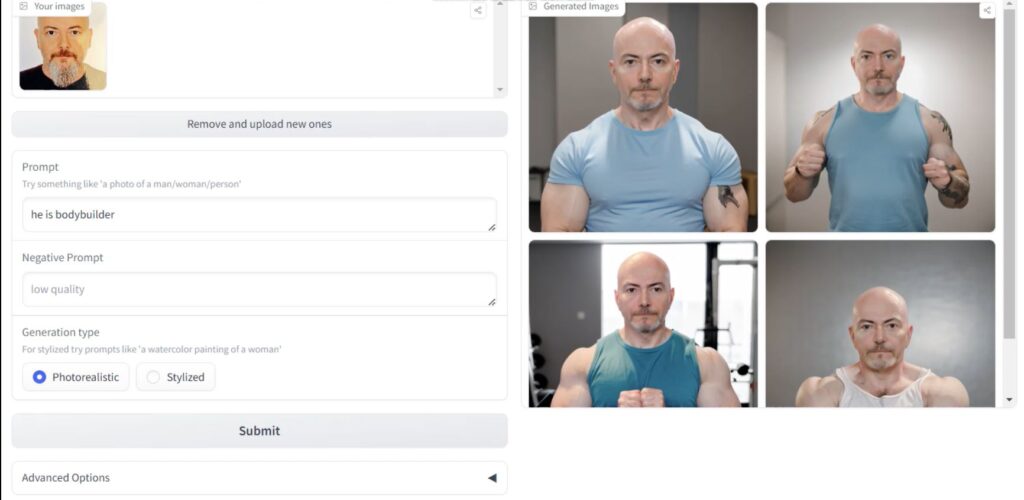
Yeni Nesil Görüntü Oluşturma
Görüntü oluşturma teknolojisi sürekli olarak gelişiyor ve bu ilerlemelerle birlikte, insanların metin tabanlı girdilerle gerçekçi görüntüler üretme yeteneği de artıyor....

İnşaat Sektöründe Big Data için Takip Edilmesi Gereken En Önemli KPI’lar
Big data, inşaat sektöründe verimliliği, üretkenliği ve güvenliği artırmak için kullanılabilecek güçlü bir araçtır. Ancak, big data’nın tam potansiyelinden yararlanmak...

İnşaat Şantiyelerinde İSG Takibi ve Acil Durum Yönetimi İçin Geliştirilen Görüntü İşleme Tabanlı Uygulama
İnşaat sektöründe güvenli çalışma koşulları sağlamak her zaman öncelikli bir hedef olmuştur. Ayrrıca proje sahalarında çalışan personel sayıları ve kırılımlarının...

“Real-Time Latent Consistency Model” ile ünlülerin yüzlerinin anlık kopyalanması
Bu model, gerçek zamanlı veri analizi ve işleme konusunda kullanılan bir yapay zeka modelidir. Temel olarak, gizli değişkenlerin tutarlılığını sağlamak...

Synergizing 3D Design and Augmented Reality: A Powerful Alliance for Collision Detection in Construction
In the ever-evolving landscape of construction, the marriage of 3D design and augmented reality (AR) heralds a new era of...
Worker Timesheet-Based IWP Revision in Construction Projects: Adding a New Dimension to Cost Control
Introduction: In construction projects, cost control, accurate budget planning, and effective management of worker performance are critical elements for project...

Navigating the Digital Frontier: What Awaits the CTO/CDO in 2024?
In the ever-evolving landscape of technology and digitalization, the role of Chief Technology Officer (CTO) and Chief Digitalization Officer (CDO)...