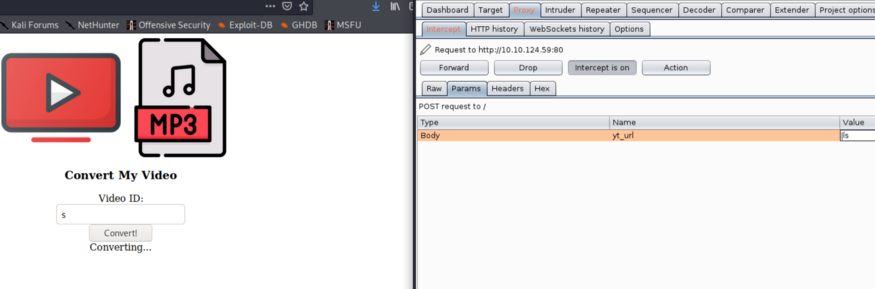
TryHackMe — ConvertMyVideo
It’s a very good lab and you can test lots of different topics at the same time; # I scan...
Unmanaged Wired Network (Kali,Ubuntu) Problemi
Kali ve Ubuntu sistemlerde grafiksel arayüz üzerinden NetworkManageri kullanmak istediğinizde wired (kablolu) bağlantı ayarlarını default olarak göremezsiniz.Eğer illada ayarları gui...
Linux Log Dosyaları
Linux sistem analizlerinde kullanabileceginiz log dosyaları ve açıklamamaları.

Aerography ile Linux Cover’ıma Kavuştum
Tekniğin adı Aerography konu hakkında en ufak bir bilgim bile yok. Arkadaşımın arkadaşı vasıtası ile bu işlemi emektar msi mega...
Metasploit Banner’ının Değiştirilmesi
Metasploit’in kendine ait her açılıştı random gelen eğlenceli bannerlarınızı hepiniz bilirsiniz. Rusyada capture flag yarışmasına katıldığımda aynı yarışaya katılan bir...
IT Security Baseline – 5 (FTP/SFTP) Türkçe
Bir çok kurumda kurulu işletim sistemleri cihazların minimum güvenlik seviyeleri belirli aralıklarla kontrol edilmektedir. Kurumlar kendi oluşturdukları güvenlik listeleri yada...
Ücretsiz ve Açık Kaynak Kodlu Araçlar Kullanılarak Geliştirilen Ağ Güvenlik Açığı Tarayıcısı (Bitirme tezim)
Savaş Saygılı Finansal Teknoloji Hizmetleri A.Ş., Murat Koyuncu Bilişim Sistemleri Mühendisliği Bölümü, Atılım Üniversitesi, Tezin orjinal linki http://www.emo.org.tr/ekler/8b7fc62a5aa1780_ek.pdf Özetçe Bu...