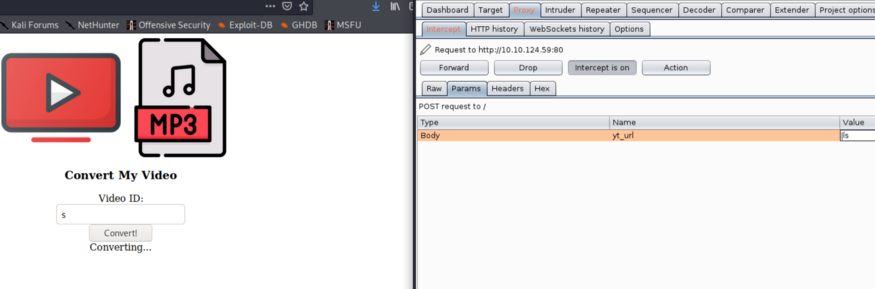
TryHackMe — ConvertMyVideo
It’s a very good lab and you can test lots of different topics at the same time; # I scan...

TryHackME — NAX- walkthrough
ROOM NAX https://tryhackme.com/room/nax Nax Identify the critical security flaw in the most powerful and trusted network monitoring software on the market,...